Tired of “Access Denied”? So are professionals. Workplace digital fences are meant to protect, but they often lock out essential tools.
The central question remains: Is there a dependable way to learn how to bypass blocked sites without violating policies or compromising your device? Yes, but it requires sophisticated tools that securely manage your digital fingerprint and connection. We’ll show you how to overcome these limitations and reveal the best solution for seamless, unrestricted access.
What Types of Sites Get Flagged and Blocked?
Network administrators typically block websites that fall into these major categories:
-
Social Media & Communication: Platforms like TikTok and Instagram are often restricted to minimize employee distraction.
-
Entertainment & Streaming: Sites like Netflix, YouTube, and online gaming portals are blocked because they consume significant network bandwidth.
-
Security Risks: High-risk sites, including anonymous proxy servers, torrent sites, and those known for malware, are banned to protect the corporate network from threats.
-
Competitive or Financial Data: Specific competitor websites or financial platforms may be blocked to prevent potential data leaks or unauthorized access.
Identifying the reason a site is blocked is the first step to bypassing it effectively and safely.
Can I Bypass Blocked Sites on a Work Computer?
Yes, you can bypass blocked sites, but traditional methods like public proxies or free VPNs usually fail because corporate networks easily detect and block them.
Relying on unapproved tools can also violate company policy. To unblock websites safely for work or legitimate personal use, you need an advanced solution that operates on a deeper technical level.
Method 1: Use a Private Browser Like RoxyBrowser
RoxyBrowser is the premier choice for overcoming persistent network limitations. It’s a dedicated platform for managing and spoofing multiple, unique digital identities, not just a simple web browser. It creates a completely isolated browsing environment for every session. This sophisticated approach makes it virtually undetectable to network protocols.
By isolating your activity, RoxyBrowser prevents cookie leaks and cross-session tracking, common methods networks use to flag users. It gives you the power to choose your own virtual identity and connection point, making any blocked site accessible with high security and anonymity.
Why Use RoxyBrowser to Unblocked Websites on Work Computer
To truly understand how a professional tool like RoxyBrowser provides the ultimate answer to how to bypass blocked sites, examine the unique features built for stealth, isolation, and control.
-
Unbreakable Digital Fingerprint Spoofing
RoxyBrowser forges a unique, full device identity for each profile, making multi-account detection impossible and ensuring you appear as a genuine user. -
Advanced IP Address Management
Easily rotate your IP address and region with the Proxy Panel to simulate human diversity and bypass advanced bot-detection systems. -
Secure Private Browsing and Session Isolation
Standard incognito or private browsing only stops local history saving; it doesn’t hide activity from the network. RoxyBrowser offers Exchange-Grade Session Isolation, fully isolating sensitive activities (wallets, DeFi) to prevent cookie leaks. -
Multi-Accounting and Profile Templates
Create customized, separate virtual identities with one click to manage numerous profiles seamlessly and avoid cross-contamination or simultaneous bans.
How to Set Up RoxyBrowser in 3 Steps
Setting up RoxyBrowser is simple.
Step 1: Download and Installation
Securely download the application and complete the installation.
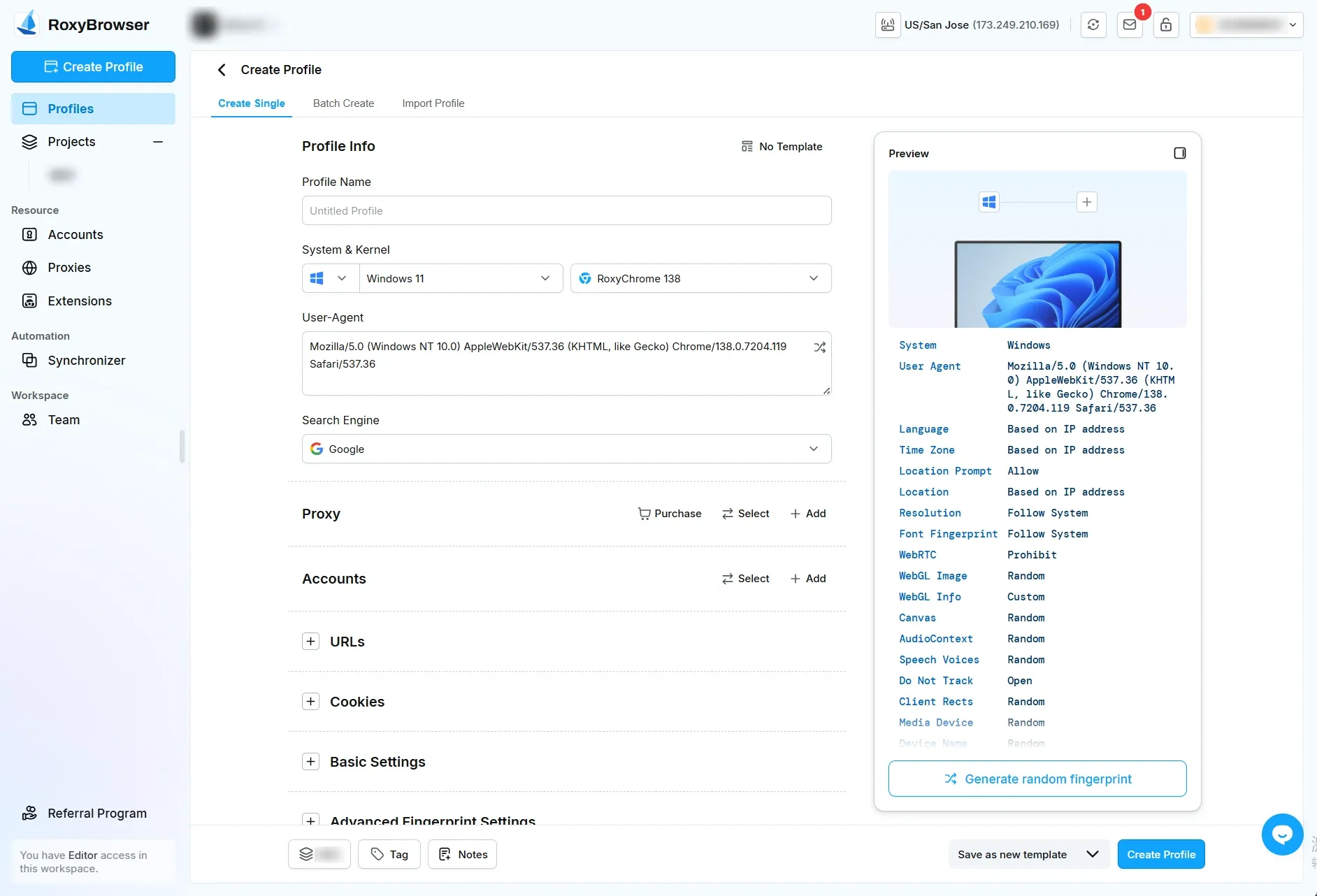
Step 2: Create a New Profile
Launch and use the Profile Template to instantly create a unique profile with an isolated digital fingerprint. You can also use the Proxy Panel within the new profile to assign a fresh IP address and geographical location
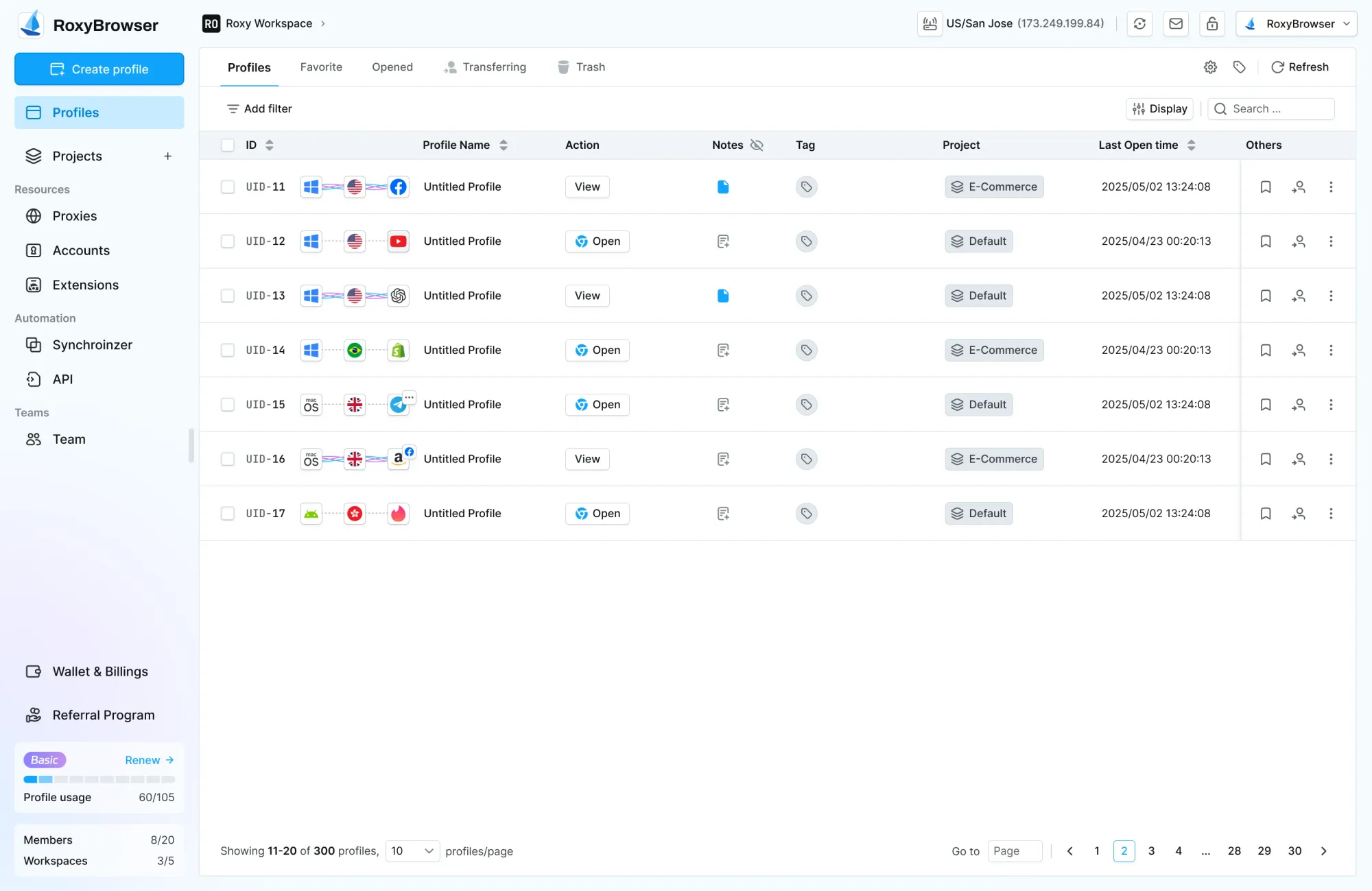
Step 3: Open the Browser and Access Blocked Sites
Click the “Open” or “View” button next to your created profile. A new browser window appears with your configured access environment. Now you can freely and securely access your the content you want!
Method 2: Use a VPN to Bypass Blocked Sites
A VPN (Virtual Private Network) encrypts your internet traffic and routes it through a remote server, masking your actual IP address. This makes it appear as if you are browsing from a different location, bypassing network-level blocks.
Step-by-Step Guide:
- Subscribe to a reputable VPN service.
- Download and install its application on your computer.
- Launch the app, log in, and connect to a server of your choice.
- Once connected, access the previously blocked site.
❌ Limitations: Corporate firewalls often detect and block known VPN IP ranges. VPNs can also slow down your connection speed and using one may violate strict company IT policies.
Method 3: Use a Proxy Unblocker
A web-based proxy acts as an intermediary between your browser and the blocked website. You enter the site’s URL into the proxy’s website, which fetches and displays the content for you, circumventing direct blocks.
Step-by-Step Guide:
- Search for a “web proxy” or “proxy unblocker” site using a search engine.
- Navigate to the proxy service’s homepage.
- Enter the URL of the blocked website into the proxy’s address bar.
- Click the “Browse” or “Go” button to view the site through the proxy.
❌ Limitations: This method offers no encryption, leaving your data exposed. Many proxies are riddled with intrusive ads, and they can be easily detected and blocked by network administrators.
Method 4: Adjust Chrome Browser Permissions
Sometimes, restrictions are applied via browser settings rather than the network. You can attempt to adjust site permissions in Chrome to regain access, though this is often reverted by admin policies.
Step-by-Step Guide:
- In Chrome, click the three dots > Settings > Privacy and security > Site settings.
- Navigate to specific permission categories like JavaScript or Pop-ups and redirects.
- Ensure the site isn’t on the “Not allowed to” blocklist.
- Alternatively, add the site URL to the “Allowed to” list.
❌ Limitations: This is a low-success method for corporate blocks. Administrative controls often lock these settings, preventing changes, and it does not bypass network-level filtering at all.
Method 5: Use an “Unblock Websites” Browser Extension
Numerous free browser extensions promise to unblock sites by acting as lightweight proxies or by manipulating DNS settings directly within your browser.
Step-by-Step Guide:
- Visit the Chrome Web Store from your browser.
- Search for terms like “unblocker,” “proxy,” or “VPN extension.”
- Select a highly-rated extension and click “Add to Chrome.”
- Follow its specific setup instructions, which usually involve toggling it on.
❌ Limitations: These extensions can pose significant security and privacy risks, as they often have access to all your browsing data. They are also frequently detected and disabled by managed corporate browser policies.
Other Important Considerations for Network Access
While RoxyBrowser provides technical support, use discretion and be aware of the company policy regarding unapproved software. Always prioritize responsible private browsing.
For advanced users, the Bot-Resistant Automation API powers scripts with advanced network features and behavioral random number generation, allowing automation tasks to proceed undetected by sophisticated filters.
Conclusion
Restricted access is no longer a barrier. Choosing the right, high-grade technology is the key to knowing how to bypass blocked sites securely. RoxyBrowser provides the advanced digital fingerprinting and session isolation needed to reliably unblock websites and maintain digital freedom.
Choose RoxyBrowser today and elevate your web journey with unbreakable access control!
